Section - Subdomain Enumeration
Notes (by task):
- Task 1 -Brief Intro
- Subdomain enumeration is just finding subdomains that exist on a domain.
- Why? It just expands the attack surface, and potentially opens more points of vulnerability
- Three main types
- Brute Force
- OSINT
- Virtual Host
- Subdomain enumeration is just finding subdomains that exist on a domain.
- Task 2 - OSINT - SSL/TLS Certificates
- When a SSL certificate is issued, the CA (Certificate Authority - Cloudflare, LetsEncrypt, etc) makes a transparency log of it.
- Searchable Databases
- These databases list the subdomain by date issued/logged
- When a SSL certificate is issued, the CA (Certificate Authority - Cloudflare, LetsEncrypt, etc) makes a transparency log of it.
- Task 3 - OSINT - Search Engines
- Simply google dorking and finding things search engines have indexed is a great way to find something.
- Ex given:
-site:www.tryhackme.com site:.tryhackme.com
- Ex given:
- Simply google dorking and finding things search engines have indexed is a great way to find something.
- Task 4 - DNS Bruteforce
- This is a method of trying tons of combos of potential subdomains (usually trying common ones in wordlists) till you end up with a list of successful/found subdomains.
- Task 5 - OSINT - Sublist3r
- Another tool to bruteforce and or use any of the above methods to automatically find subdomains
- Task 6 - Virtual Hosts
- Since some subdomains aren’t listed in a public DNS record, sending a request directly to a host machine (via IP, etc) can sometimes result in finding something such as a development subdomain, or other non-public subdomains.
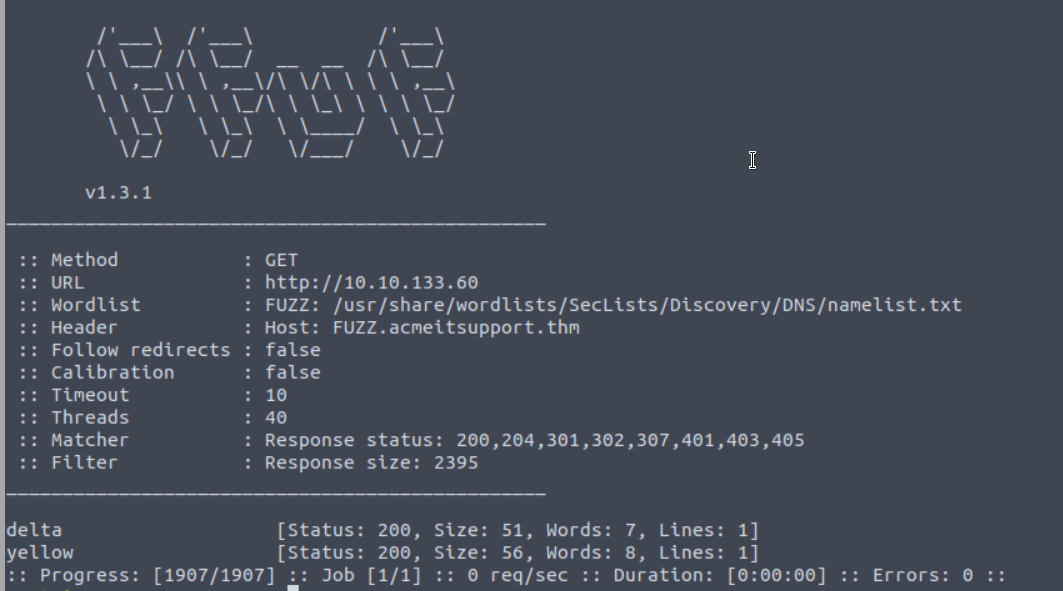
- This usually is done via a tool, thm used
ffuf. - A webserver will often send a successful/valid result on every query, so checking the size of the response is important to filter out data that isn’t helpful or relevant.
- This usually is done via a tool, thm used
- Since some subdomains aren’t listed in a public DNS record, sending a request directly to a host machine (via IP, etc) can sometimes result in finding something such as a development subdomain, or other non-public subdomains.
Screenshots
Result of the ffuf tool in task 6